
Operational technology systems are certainly not one size fits all, and we understand that everyone faces different cybersecurity challenges in industrial environments.
Set up some time with one of our experts to see how our OT cyber risk management platform can help solve your unique security needs. Our solution can help you with:
Industrial Defender safely collects, monitors and manages your OT assets at scale using agent, agentless or passive data collection methods.
Watch now
We combine accurate software inventory data with the power of NIST’s vulnerability database and ICS-CERT alerts.
Watch now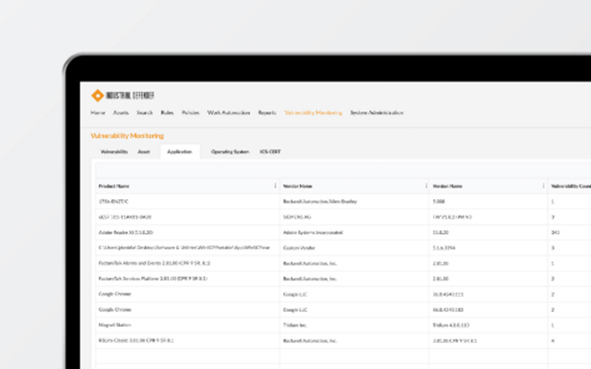
Industrial Defender enables OT teams to manage configuration rules and monitor for changes in an asset’s configuration. View this demo video to learn how our solution helps you manage configuration changes across your entire OT asset base.
Learn more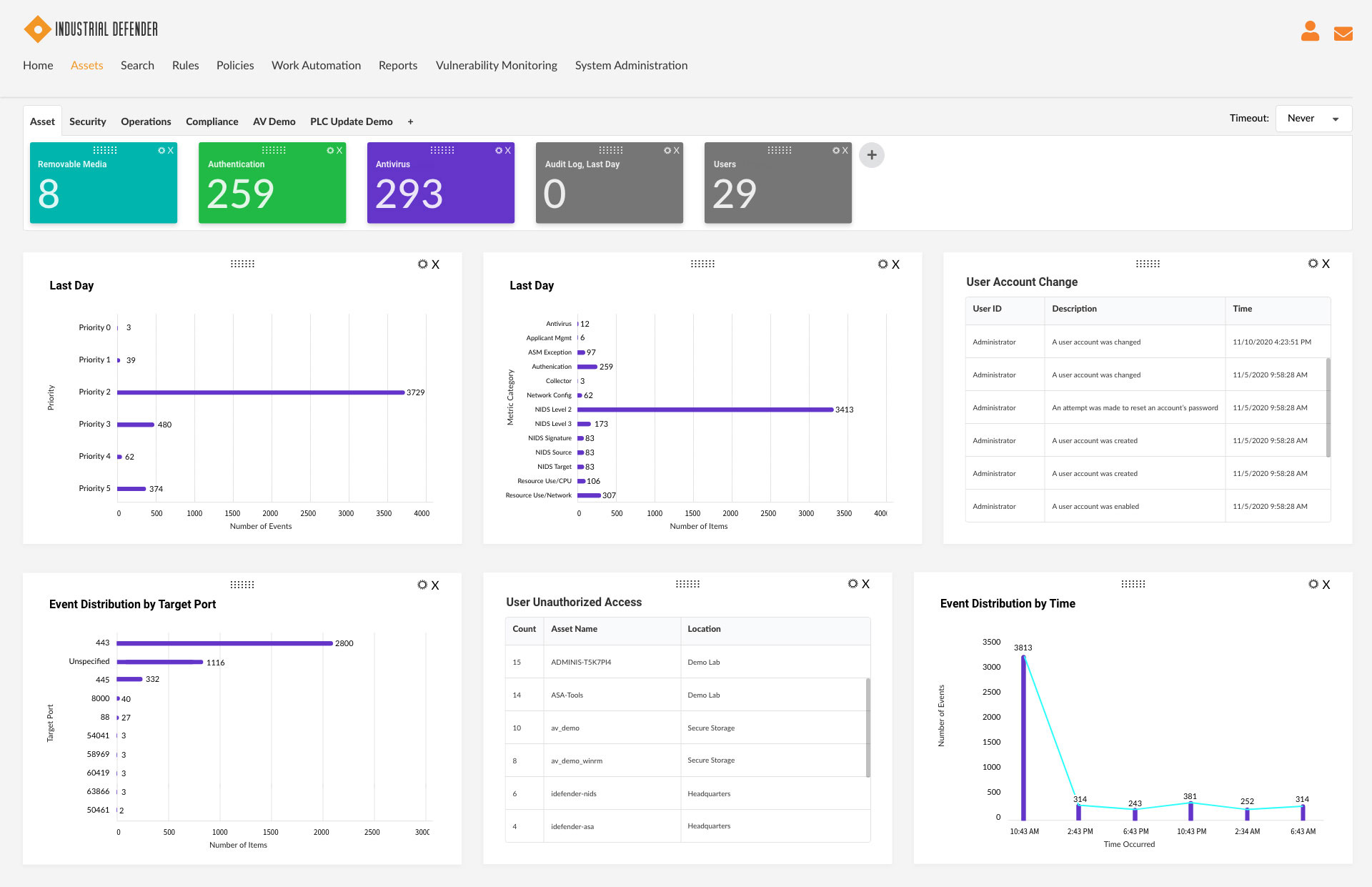
The ID + Splunk app increases the effectiveness of using Splunk in OT environments by helping analysts to quickly identify and mitigate potential cybersecurity issues.
Watch now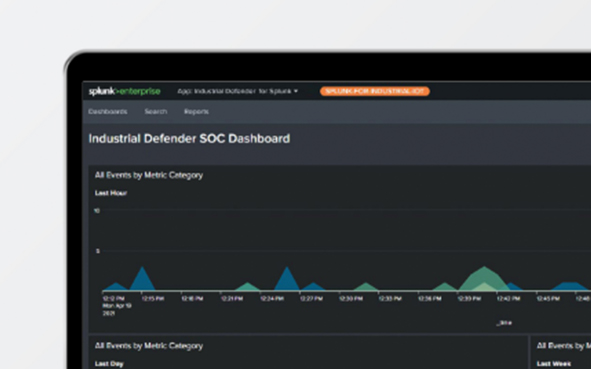
Provide the critical data you need to prove compliance with your standard using our pre-built multi-national compliance reports or create your own with our custom reports.
Learn more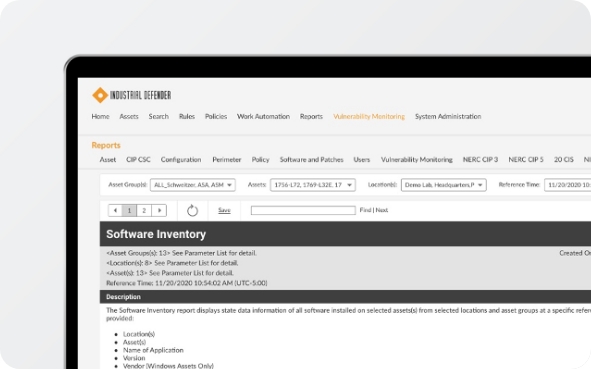
Sign up for our newsletter to receive the latest
Industrial Defender news, updates and content.