When assessing vulnerabilities in ICS/OT environments, a different approach is required compared to traditional IT. Industrial Defender recognizes the unique design, context, and critical nature of OT assets, offering an operationally safe method for identifying and prioritizing vulnerabilities. Our platform provides an accurate, complete, and up-to-date view of vulnerabilities across your OT environment and intelligently prioritizes your remediation efforts based on the potential impact to your specific environment.
Know immediately if your asset is at risk without waiting for the next software update
Prioritize risk mitigations with our Vulnerability Prioritization Engine
Share OT vulnerability data across functions to make smarter patching decisions
Get a personalized demonstration of what our solution can do for your team.
Learn moreView videos of our solution based on your unique challenges.
Learn moreAccess additional vendor-approved data via our strategic partnership
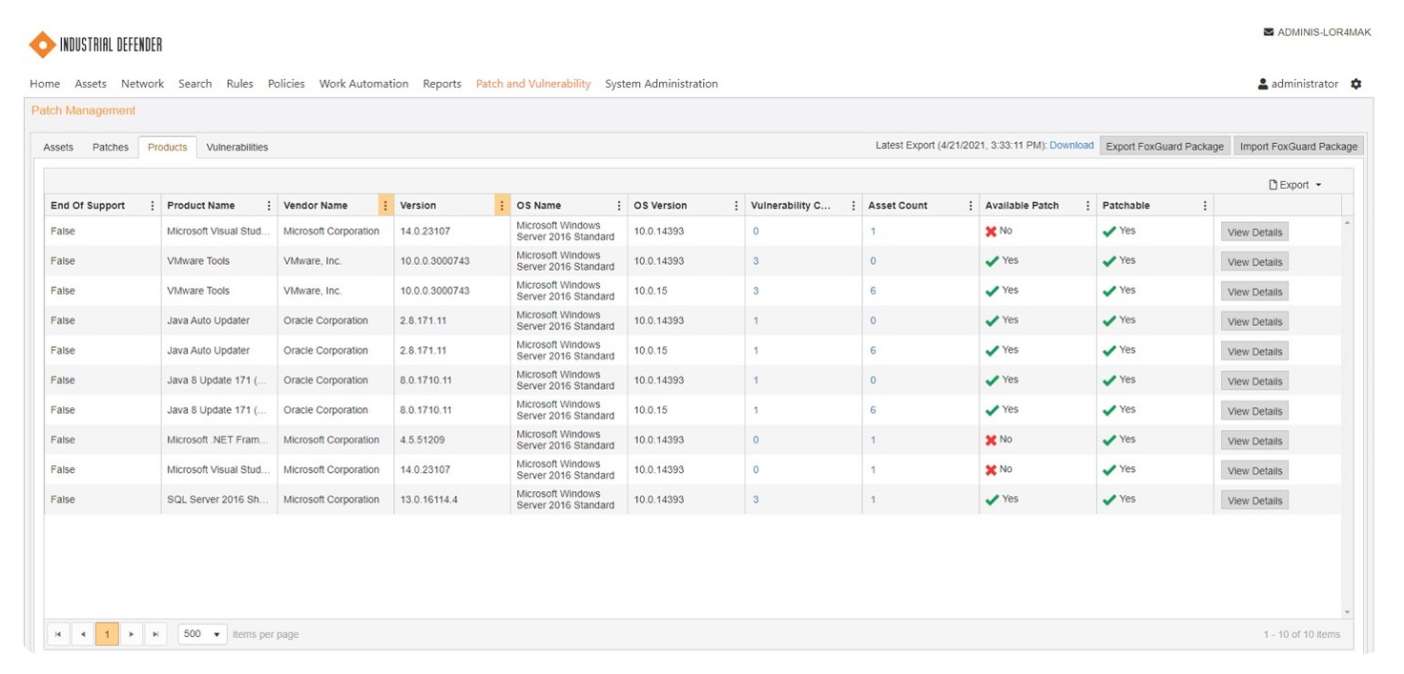
Visualize precisely which assets are missing critical vendor patches or have open vulnerabilities published in vendor feeds
Track patches from release to installation, including a security rating for each